
Details
Threat Intelligence
Introduction
In recent years, cyberthreat intelligence has become an important supporting pillar in a mature cybersecurity strategy. When applied well, threat intelligence can help security teams defend against an ever-more sophisticated threat landscape before, during and after attack.
By studying adversaries and understanding their strategies and objectives, organizations can build more effective, more refined and more robust cyberdefenses.
The Internet, the network or networks is huge and has the most significant data you can ever think about; it is not limited to search the people or company information only, but it has the potential to predict the future happenings.
The said prediction is based on data, that you need to process for the information, the job of an OSINT professional is to connect the data points and draw a meaningful conclusion.
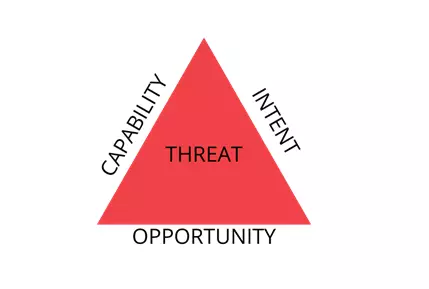
Threat is anything that can potentially harm the business operation or continuity; threat depends on three core factors:
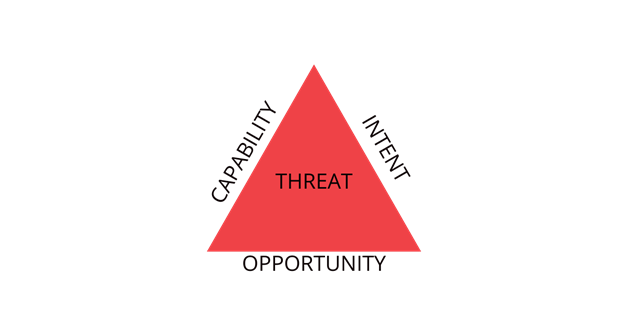
- Intention: A desire or objective.
- Capability: Resources that support the intention
- Opportunity: Right timing, technique, procedure, and tools
Frequently, associations neglect to recognize the risk, and they generally spend a lot on fixing the vulnerabilities and researching the issues after the attack, rather fixing it before it shows up.
Threat intelligence, as Gartner defines: “evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject’s response to that menace or hazard.”
Threat Intelligence is a critical security tool that uses global security intelligence to detect malicious activity inside your network.
It is an act to predict (based on the data) the upcoming attacks against an organization. Though, open source risk knowledge alludes the way toward utilizing freely accessible sources to foresee the actor or potential activity (threat). Cyber threat intelligence helps you to make better decisions about your defense and other benefits along:
- Adopt a proactive approach instead of reactive; you can create the plan to fight against the current and future threats.
- Organize the security alert mechanism, enables you to secure before you get attacked.
- Always provide the better response to the security incidents
- Use the cyber intelligence feeds to provide your security technologies up-to-date information to block the emerging threats
These solutions can take a number of different forms. Threat intelligence feeds take security data from vendors, analysts and other sources about threats and unusual activity happening all around the world. Malicious IP addresses, domains, file hashes and other data stream in constantly from external parties. This can help companies understand behaviors that might be affecting their own networks.
Threat intelligence platforms (TIPs) take this a step further. They incorporate one or many data feeds and subject the data to detailed analysis. Advanced analytics are used to isolate unusual patterns in systems and mine other valuable data.
At a minimum, a threat intelligence platform should have actionable indicators that can be used to identify potential threats to an organization (such as known bad IP addresses and URLs, and malware hashes), and support collaboration and investigation workflow for the security analyst and broader community.
Let’s have a look at The Life Cycle of Threat Intelligence:-
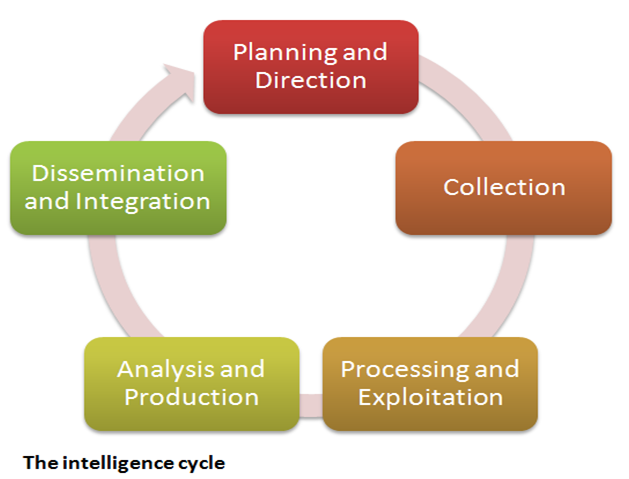
So, how does cyber threat intelligence get produced? Raw data is not the same thing as intelligence — cyber threat intelligence is the finished product that comes out of a six-part cycle of data collection, processing, and analysis. This process is a cycle because new questions and gaps in knowledge are identified during the course of developing intelligence, leading to new collection requirements being set. An effective intelligence program is iterative, becoming more refined over time. To maximize the value of the threat intelligence you produce, it’s critical that you identify your use cases and define your objectives before doing anything else.
1. Planning and Direction
The first step to producing actionable threat intelligence is to ask the right question.
The questions that best drive the creation of actionable threat intelligence focus on a single fact, event, or activity — broad, open-ended questions should usually be avoided.
Prioritize your intelligence objectives based on factors likehow intently they cling to your association's fundamental beliefs, how huge of an effect the subsequent choice will have, and how time delicate the choice is.
One significant managing factor at this stage is understanding who will devour and profit by the completed product — will the knowledge go to a group of analyst with specialized expertise who need a quick report on new exploit, or to an official that is searching for an expansive review of patterns to illuminate their security venture choices for the following quarter?
2. Collection
The next step is to gather raw data that fulfills the requirements set in the first stage. It’s best to collect data from a wide range of sources,interior ones like system event logs and records of past incident reactions, and outside ones from the open web, the deep web, and technical sources.
Threat data is typically thought of as records, for example, malicious IP addresses, domains, and document hashes, yet it can likewise include vulnerable data, for example, the data of clients, source code from sites, and content from news sources or Internet(Social Media).
3. Processing
When all the raw information has been gathered, you have to sort it, arranging it with metadata labels and filtering it through repetitive data or false positives and negatives.
Even, today associations gather information on the request of a huge number of log events and a huge number of markers consistently. It's a lot for human analyst to process productively — information gathering and handling must be mechanized to in order to understand it properly.
Arrangements like SIEMs are a decent spot to begin since they make it moderately simple to structure information with connection decides that can be set up for a couple of various use cases, however they can just take in a set number of information types.
In case you're gathering unstructured information from various inward and outside sources, you'll need an increasingly vigorous arrangement. Recorded Future uses AI and regular language preparing to parse content from a huge number of unstructured archives crosswise over seven distinct dialects and arrange them utilizing language-free ontologies and events, empowering investigators to perform amazing and natural pursuits that go past uncovered watchwords and basic connection rules.
4. Analysis
The next step is to make sense of the processed data. The goal of analysis is to search for potential security issues and notify the relevant teams in a format that fulfills the intelligence requirements outlined in the planning and direction stage.
5. Dissemination
The product is then distributed to its intended consumers. For threat intelligence to be actionable, it has to get to the right people at the right time.
It also needs to be tracked so that there is continuity between one intelligence cycle and the next and the learning is not lost. Use ticketing systems that integrate with your other security systems to track each step of the intelligence cycle — each time a new intelligence request comes up, tickets can be submitted, written up, reviewed, and fulfilled by multiple people across different teams, all in one place.
6. Feedback
The final step is when the intelligence cycle comes full circle, making it closely related to the initial planning and direction phase. After receiving the finished intelligence product, whoever made the initial request reviews it and determines whether their questions were answered. This drives the objectives and procedures of the next intelligence cycle, again making documentation and continuity essential.
The Types of Threat Intelligence
As demonstrated by the threat intelligence lifecycle, the final product will look different depending on the initial intelligence requirements, sources of information, and intended audience. It can be helpful to break down threat intelligence into a few categories based on these criteria.
Threat intelligence is often broken down into three subcategories:
- Strategic - Broader trends typically meant for a non-technical audience
- Tactical - Outlines of the tactics, techniques, and procedures of threat actors for a more technical audience
- Operational - Technical details about specific attacks and campaigns
Here are top threat intelligence platforms -some offer a free version for lower-volume users. The vendors covered in this guide are those that most closely meet the criteria for threat intelligence platforms as laid out by Forrester Research in Rules Of Engagement: A Call To Action To Automate Breach Response and Vendor Landscape: External Threat Intelligence, 2017.
Key features include the consolidation of threat intelligence feeds from multiple sources, automated identification and containment of new attacks, security analytics, and integration with other security tools.
- IBM X-Force Exchange
- AnomaliThreatStream
- Palo Alto Networks AutoFocus
- RSA NetWitness Suite
- LogRhythm Threat Lifecycle Management (TLM) Platform
- FireEyeiSIGHT Threat Intelligence
- LookingGlass Cyber Solutions
- AlienVault Unified Security Management (USM)
- Honorable Mentions
Honorable Mentions:-
1. SolarWinds Threat Monitor offers threat intelligence, SIEM, log correlation and analysis, network intrusion and host intrusion detection systems.
2. Cisco Threat Intelligence Director (TID) is a feature in Cisco's Firepower Management Center (FMC) product offering that automates the operationalization of threat intelligence. TID serves Cisco's Next Generation Firewall (NGFW) product.
3. SonicWall Network Security services platform includes real-time threat intelligence from the aggregation, normalization, and contextualization of security data.
4. Crowdstrike Falcon integrates threat intelligence into endpoint protection, automating incident investigations and speeding breach response. It is supported by the CrowdStrike Falcon Intelligence team.
5. ThreatConnect provides intelligence, automation, analytics, and workflows in one platform.
6. Symantec DeepSight Intelligence consists of visibility provided by the Symantec Global Intelligence Network, the largest civilian threat collection network and tracks over 700,000 global adversaries.
7. LookingGlass Strategic Intelligence Subscription Service offers a digital library of actionable and relevant finished intelligence reports, augmented by analysts who enrich the data feeds and provide timely insights.
8. Accenture iDefense provides security intelligence through the IntelGraph platform that provides context, visualizations, advanced searching and alerting.
9. Proofpoint Emerging Threat (ET) Intelligence provides threat intelligence feeds to identify suspicious or malicious activity.
10. McAfee Advanced Threat Defense includes threat intelligence sharing to locate hidden threats.
11. CenturyLink Analytics and Threat Management gives uses access to actionable, prioritized threat data that is correlated to customer IP addresses.
12. Imperva Threat Intelligence combines threat research from Imperva security researchers, threat intelligence from a variety of partners, and live data crowdsourced.
13. Check Point ThreatCloud combines threat prevention technology with threat analysis to prevent attacks.
References:-
https://www.blueliv.com/blog/threat-intelligence/what-is-threat-intelligence/
https://www.recordedfuture.com/threat-intelligence/
https://resources.infosecinstitute.com/open-source-threat-intelligence-tools-techniques/#gref
https://www.esecurityplanet.com/products/top-threat-intelligence-companies.html
https://www.forrester.com/report/Vendor+Landscape+External+Threat+Intelligence+2017/-/E-RES136769?objectid=RES136769
https://countuponsecurity.files.wordpress.com/2015/08/intelligencecycle.png
